Are you GDAP ready?
22 June, 2023
Microsoft recently reinforced customer access control capabilities by introducing a new Zero Trust feature, Granular Delegated Admin Privileges (GDAP).
If you are a Microsoft direct partner, indirect provider, or indirect reseller, moving to Microsoft GDAP is essential.
GDAP reduces the security risks and vulnerabilities, allowing partners to set up granular and time-bound access to the workloads of their customer tenants.
While GDAP is not a new concept, there are some important milestones approaching in the implementation of GDAP. Partners will need to act to avoid losing administrative access to their customer tenants.
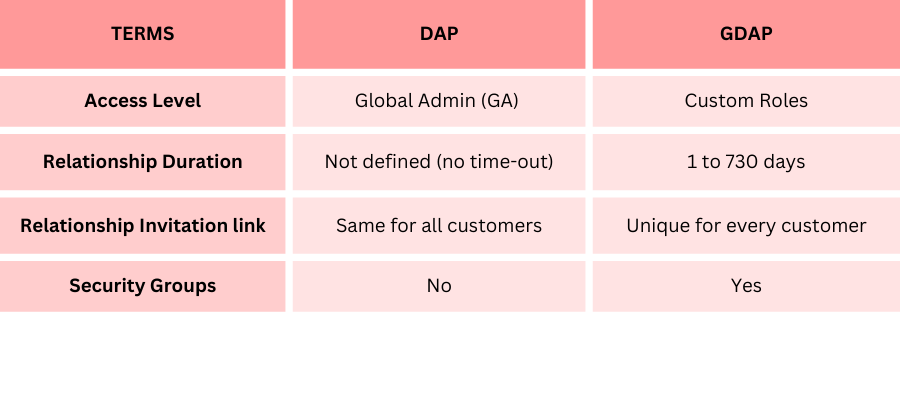
GDAP vs DAP
Access, and roles
In the current existing DAP, by default, the partner is granted the role of the global admin (GA), giving them full access to their customer’s data and workloads. This relationship is an ‘all or nothing’ approach, where the partner has either full access or no access across all the customer tenants. This is a major security concern that should the partner’s account be compromised; the customer’s data will also be exposed.
With GDAP, customer tenants no longer need to provide admin level access to the partner. They can narrow the scope of access to its data and workloads by giving specific permissions to partner roles within Azure AD. These roles can be different for each customer, and can be mutually agreed on between partner and customer tenant.
Relationship duration
In DAP, the relationship between the partner and customer tenant is indefinite (no time-out) with Microsoft.
The way DAP works is that when you onboard a customer you may see many different partner relationships on the tenancy from existing services that were provided either through a previous indirect, direct, or Microsoft provider. All these relationships remain residual on the tenancy even years after those service providers no longer provide licenses or direct support but they will still have full Global Admin access to the tenancy, and the ability to interact.
GDAP has a defined relationship duration ranging from 1 day to 730 days (2 years).
By limiting the access and duration to only the current service provider or to those who need access is an important security measure and certainly why GDAP is reinforced.
Pro tip: The GDAP relationship does not auto renew and will require the partner to renew it before each defined duration ends.
Invitation link
When setting up GDAP permissions, the invitation link sent to the customer tenants for access is unique to each customer. The customer tenant will have the ability to approve or not, the access level given to the partner.
Security groups
Partners have the ability to assign different levels of the customer’s account access to different groups or individuals within the organisation. Each security group or individual will be given specific or multiple role permissions i.e. Group 1 whose role is to look after compliance will be assigned the compliance admin role or Group 2 whose role is help desk will be assigned the help desk role.
Pro tip: The security group access levels will not be visible to the customer tenant.
The impact on new and existing customer tenants
In the current process, when creating a new customer tenant, GDAP is optional and must be actioned separately. When GDAP relationship is established, it will take precedence over DAP.
For existing customer tenants, Synnex will be transitioning them to GDAP by the end of May. This process will be automatic and no partner intervention is required.
Partner call-to action: The partner will need drive their own GDAP relationships with their customer tenants by defining the roles, and activating this with each customer tenant.
Make use of the GDAP bulk migration tool for faster integration.
The Microsoft led GDAP transition factors in a baseline level of core admin roles for service providers as best practise. This allows the provider the capabilities to facilitate support for scenarios like accidental change of configuration, recovering accounts where partners have lost access to their tenants due to lost passwords, or multi-factor authentication, password resets, and other basic administration support.
Key dates
January 2023: Invitations to transition to GDAP sent out to partners
19 May: Synnex migration of existing customer tenants to GDAP
22 May: Microsoft led transition moves all existing customer tenants from DAP to GDAP
End June: Synnex will disable inactive DAPs from customer tenants who have established a new GDAP permission
July: Microsoft will delete inactive DAPs from customer tenants who have established a new GDAP permission
Conditional access policy
When partners set up policies to limit access to only certain users who are part of their tenant or to trusted IP addresses, it limits the service and support scope of the service provider. It also limits the ability for the service provider to enable GDAP.
Partner call-to action:
Exclude Synnex (synnexcsp.onmicrosoft.com) from conditional access policies i.e. external partner access, location, or IP based etc that may restrict roles and capabilities defined through GDAP to assist your customer tenants.
Source and credit:
Some content in this article is extracted from ‘Introduction to GDAP’ webinar on 17 May 2023.



Leave A Comment