Reach new levels of cybersecurity success and what that would look like with CSAT
29 September, 2022

From a security and governance standpoint, many of today’s MSPs are pushed to look at building a security portfolio because of the demands from shareholders and their downstream clients to meet security and compliance standards, and manage risks from the constantly evolving complexity of cyber-attacks.
Understanding where your client’s current vulnerabilities exist, and which are priority, allows your IT team to make better informed decisions about your client’s resources and security expenses.
What a cybersecurity risk assessment does is to provide a holistic view of your client’s cybersecurity position through identifying, analysing, and evaluating.
A simple regular assessment will quickly provide an insight into the potential cyber risks, identify areas of weaknesses, gaps, and where to improve your client’s security measures.
Using this assessment can provide an important baseline documentation guide to maximise and build your client’s security project pipeline.
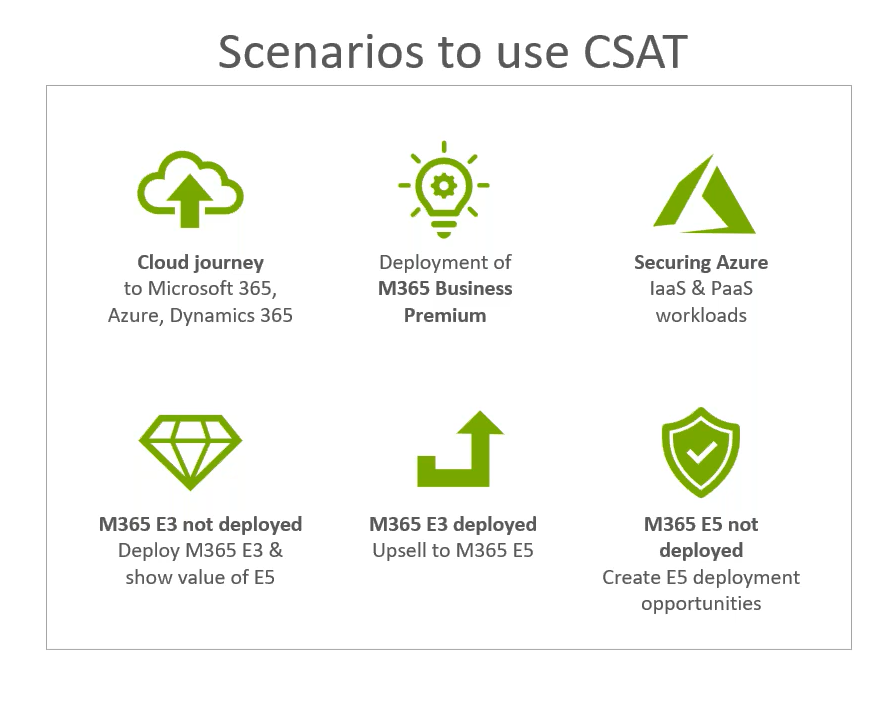
What is Cyber Security Assessment Tool (CSAT)?
QS Solution’s CSAT is a security assessment tool widely used by Microsoft partners to quickly assess the current status of their client’s security and recommend improvements based on data insights.
What does the technology look like?
CSAT runs as a dissolving agent within the client’s IT environment which allows it to have full control over where the data goes to, and who can access the data.
In a scenario where your client is working with you, you can guide your client through the set-up steps in CSAT or where it’s a managed service, you can work directly in your client’s environment.
The assessment also makes use of a survey you will conduct with IT decision makers within your client’s organisation and combines this information with data from the scan to provide powerful insights.
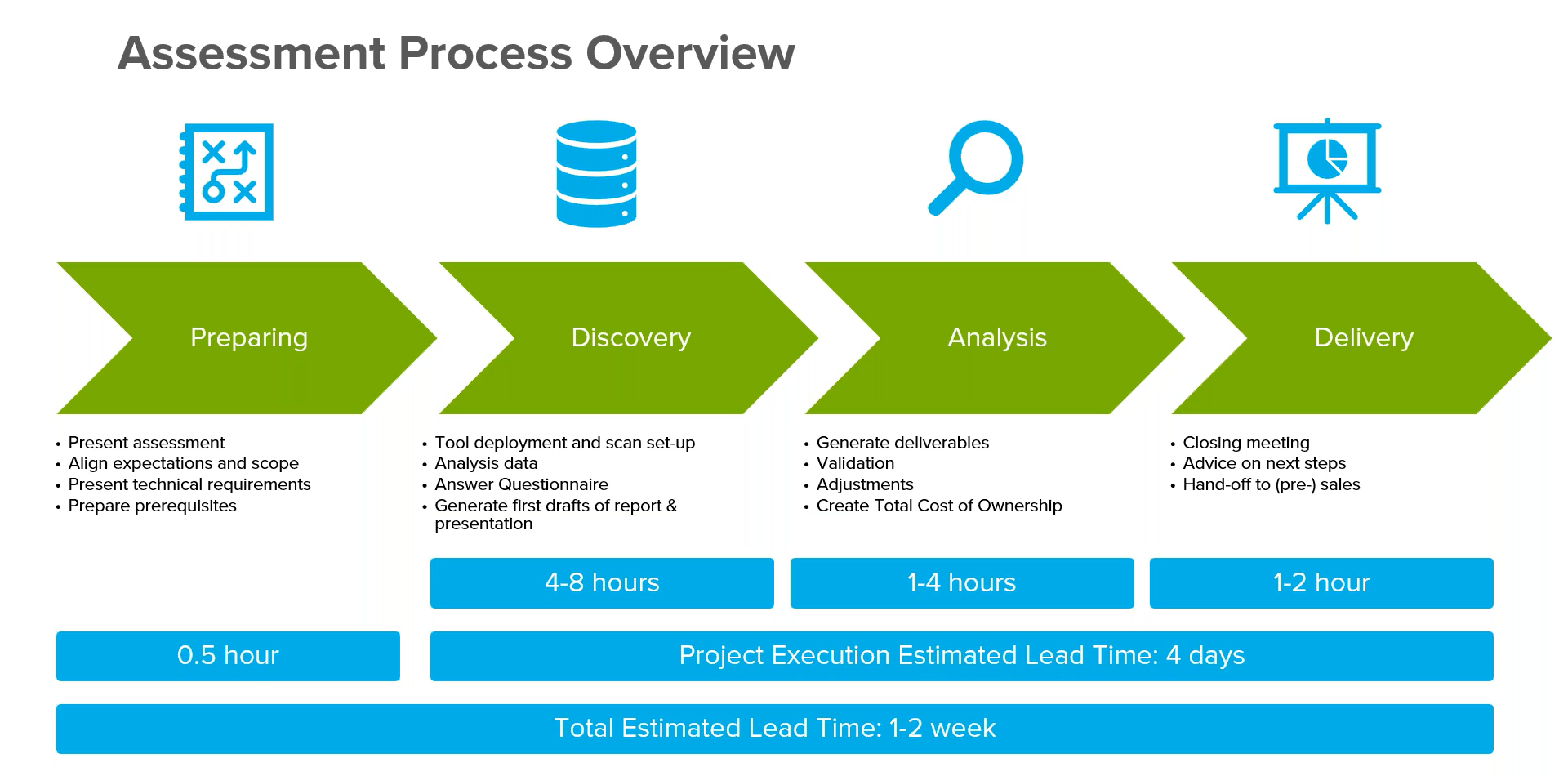
The CSAT Assessment process
CSAT offers 2 types of assessments, a full scan and quick scan.
The full scan works for SMB, Corporate, and Enterprise, providing alignment between business and IT management, helping decisions on new security initiatives, deployment, and implementation plans based on the CIS IG2 and IG3 Zero Trust framework.
Quick scan as the name suggests gives you a quick check on basic security, propose improvement actions based on actual data, and is aligned to CIS IG1 for SMB.
The assessment process is usually quite straight forward and quick, from preparing the scope of requirements and expectations, to deploying the CSAT tool to set up different automated scans from sources such as end points, local active directory, share point on premise or email DNS, analysing the data collected which gives you the structure and input to generate a 1st draft cyber security report.
CSAT uses a questionnaire based on the internationally recognised CIS framework to collect data about organisational controls, policies and other key indicators.
Customisation can be done to include total cost of ownership (TCO), an additional module on top of CSAT, which gives you the opportunity to start a conversation around investment and finance as part of your clients’ security remedial actions.
Depending on whether it’s a full or quick scan, and how much customisation you are adding to the report, the assessment ranges between a few hours, up to a week for comprehensive reports.
Pro tip: During the client report delivery, make sure your sales team is involved in the client hand off, so that they can dive straight into a discussion of necessary projects and actions required to improve your client’s security posture. Depending on the remediation required, they may need to discuss new managed services, implementation services, or licenses requirements.
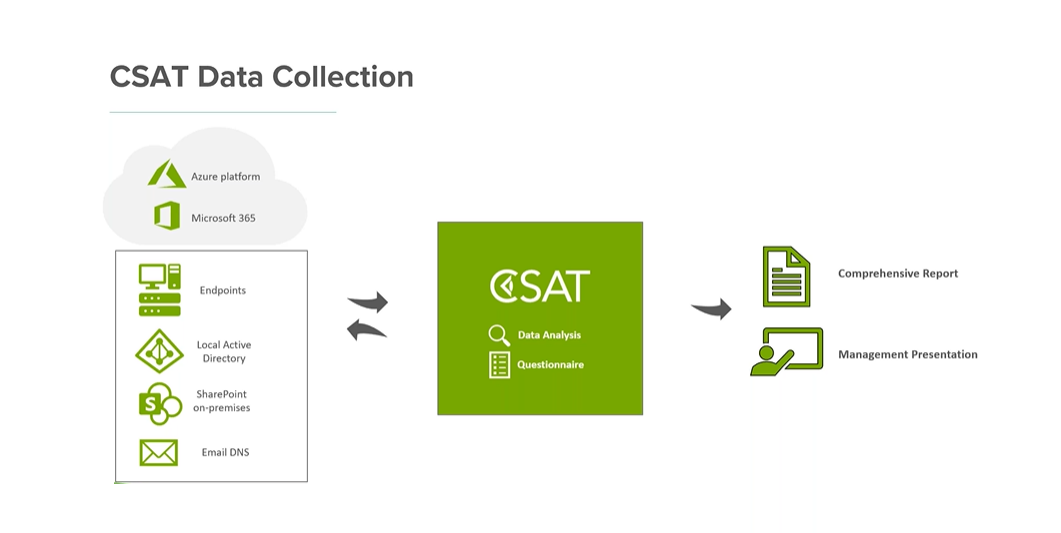
CSAT data collection
CSAT collects data from hybrid IT environment incorporating both local devices and infrastructure, as well as Microsoft Cloud products and services (Azure and Microsoft 365) and provide technical data driven recommendations such as:
- Company score based on CIS controls v8 (International recognised framework of internet security)
- Migration plans to improve cybersecurity based on Zero Trust Architecture
- Urgent action items and quick wins to start smaller projects
- Risk based action plans for improvements
- Total costs of ownership for security
CSAT deliverables
CSAT assessments provide 2 types of deliverables:
- A comprehensive report – an editable Word document that allows you to make changes where you need to. It includes urgent action lists (for IT projects or larger remedial actions) and quick wins (for existing licenses and limited investments).
- A management presentation – an editable PowerPoint presentation that focusses on the risks found and the remedial actions. It includes an overall company scoring, next steps, and recommendations.
Templates can be built within the CSAT portal for both of these deliverables, addressing your specific company objectives, further reducing the manual work required to produce documentation to present to your client
The company scoring in the CSAT report is a complete scoring model based on the CIS framework consisting of 18 controls. The client is scored on a scale of 1 to 4 with 1 meaning no measures implemented and a 4 being proactive i.e. monitoring and alerts implemented, with responsibilities taken by senior management.
While it is not expected for an organisation to hit a score of 4 for every control, what they should at least do is to decide on what risks is acceptable to their business and where they should take remedial action.
Need to know: While CSAT uses the CIS framework, there is freedom for you to map ASD Essential Eight into the CSAT report. In Essential Eight, six out of the eight Essential Eight topics are already covered in the CIS framework in detail. The maturity scoring of Essential Eight and CIS is very much aligned. You can map Essential Eight scoring 1-3 to CIS scoring 2 to 4. Essential 8 mapping can even be built into your customised templates.
Zero trust architecture
Zero trust architecture is a mindset that helps organisations to start implementing the right safe guards. It requires operational capabilities that: Never trust, always verify – treat every user, device, application, and data flow as untrusted.
In CSAT, urgent action items, quick wins, remedial actions, and recommendations are mapped back into the Zero-trust architecture zones.
While CIS is the framework to conduct security assessments to see where the organisations cyber security maturity is at, the actions and advises that comes out of this assessment should be implemented with a Zero-trust architecture.
This allows partners to be able to take the conversation forward with a holistic overview of their clients’ security position, where their risks lie, and allowing them to make informed decisions to start integrating remedial actions into their security policy.
Adding value to your security portfolio, cloud migration, and managed services
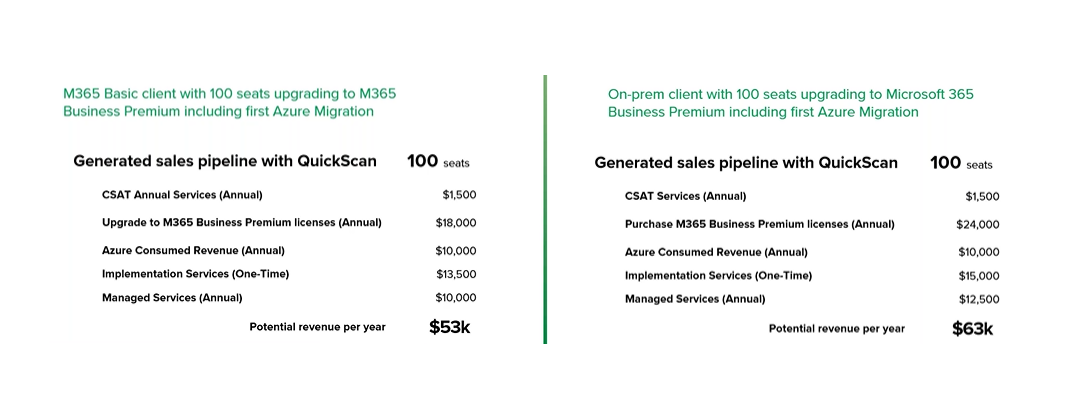
MSPs can create real opportunities to upsell and deploy licenses, products, and services like M365 licenses, Azure migration, managed services, and security solutions, and build CSAT into a recurring revenue service by continuing to work with your clients on remediation and performing periodical scanning and reporting.
So, what does the CSAT ROI looks like? Let’s look at 2 examples of the potential revenue per year with just one CSAT license:
Pro tip: Extend your MSP value to your client into the financial investment with the CSAT Security Total Costs of Ownership (TCO) module which can help shorten the sales cycle or into other cross solution areas like modernisation and migration. To take the next natural progression step, speak to a Synnex CSP expert.
Source and credit:
Some content in this article is extracted from ‘Secure and improve cybersecurity with CSAT‘ webinar held on 1 September 2022.



Leave A Comment